|
|
Order by Related
- New Release
- Rate
Results in Title For forms authentication timeout
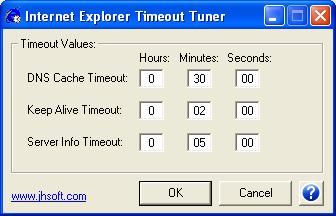 | This tool can adjust 3 'hidden' registry settings of Internet Explorer to control caching of DNS records, server connection timeout, and caching of server information.
It can be useful to change these settings to very low values, especially when testing web-servers with quickly changing DNS records / IP addresses. For example in DNS Round Robin or Simple Failover setups.
Internet Explorer does not honor and does not use the TTL (time to live) value provided in DNS records. Instead it caches all DNS records for a fixed period of time (as per this setting) - with one exception:
After Internet Explorer has fetched a web-page, it does not immediately close the TCP connection to the web-server. By keeping the connection open, following requests to the same web-server can be executed faster. This is known as 'keep alive'.
This setting affects both DNS caching and server connections ('keep alive') timeouts.
Internet Explorer does not refresh DNS records if another page is requested from the same server domain name within this time interval - even if the DNS Cache Timeout setting has a lower value.
In other words, DNS records timeout according to the higher value of this and the DNS Cache Timeout setting.
However, server connections appear to timeout according to the lower value of this and the Keep Alive Timeout setting.
So for the most predictable results, the value of this setting should be set lower than or equal to the DNS Cache Timeout setting, and higher than or equal to the Keep Alive Timeout setting. .. |
|
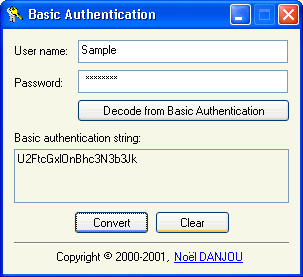 | Basic Authentication is a little program that converts a user name (login) and optionally a password to/from their Base64 Basic Authentication counterpart. ..
|
|
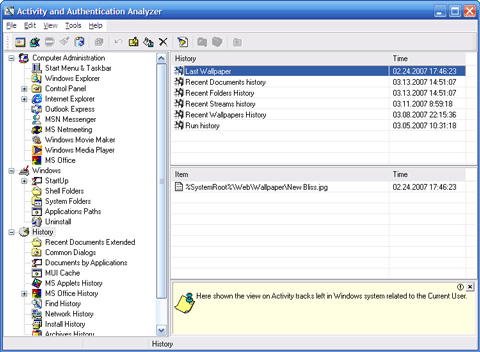 | Your PC keeps records of both your online and off-line activity. Any of the Web Pages, Movies, Pictures, Sounds, E-mail and Everything Else you have ever viewed could easily be recovered - even after many years passed! This is a serious threat to the legitimate user's privacy. Activity and Authentication Analyzer is a solution to this problem. AAAnalyzer is the powerful security software, which has been primarily destined to comprehensive search, analysis, and safe and secure deletion of the user activity traces left after work. The activity analysis and authentication or how it is called in brief statistics, as the method of information (intelligence data) collection is applied either for the preliminary exploring or when the access to information (posted message, telephone talk) is impossible or unwanted. As applied to the computer security topics the activity analysis and authentication is performed when it is impossible to get document copies, which user worked on, for example, stored either on ciphered or dismounted disk containers. Nevertheless, nothing is disappeared without any trace and it is possible, therefore, to disclose much useful data from the document; names, Internet addresses, which were visited, the application names which were launched or file names which were searched, last user's logon name. Windows 9x/NT/2000/XP/2003 has the system registry database, which is useful, for the first, to the very OS, but, for the second, for keeping many traces (evidences in other words) left by routine work and for either exploration, or for reconstruction of users activity. This software needs additionally only Internet Explorer version 4 and higher installed for proper work. Its built-in functionality allows to search the traces left in system registry, edit or fill with blanks values stored in registry keys related to the activity and authentication analysis, eradicate them in safe way, keep search log-files, and backup and restore made changes .. |
|
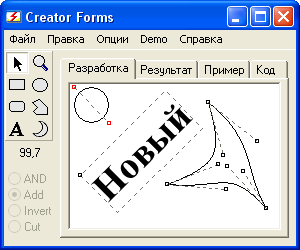 | Creator Forms the excellent assistant in creation of windows of the non-standard form for programs developed on VB. Accessible tools: rectangulars, ellipses, polygons and, attention, the TEXT and polygons with CURVE edges. ..
|
|
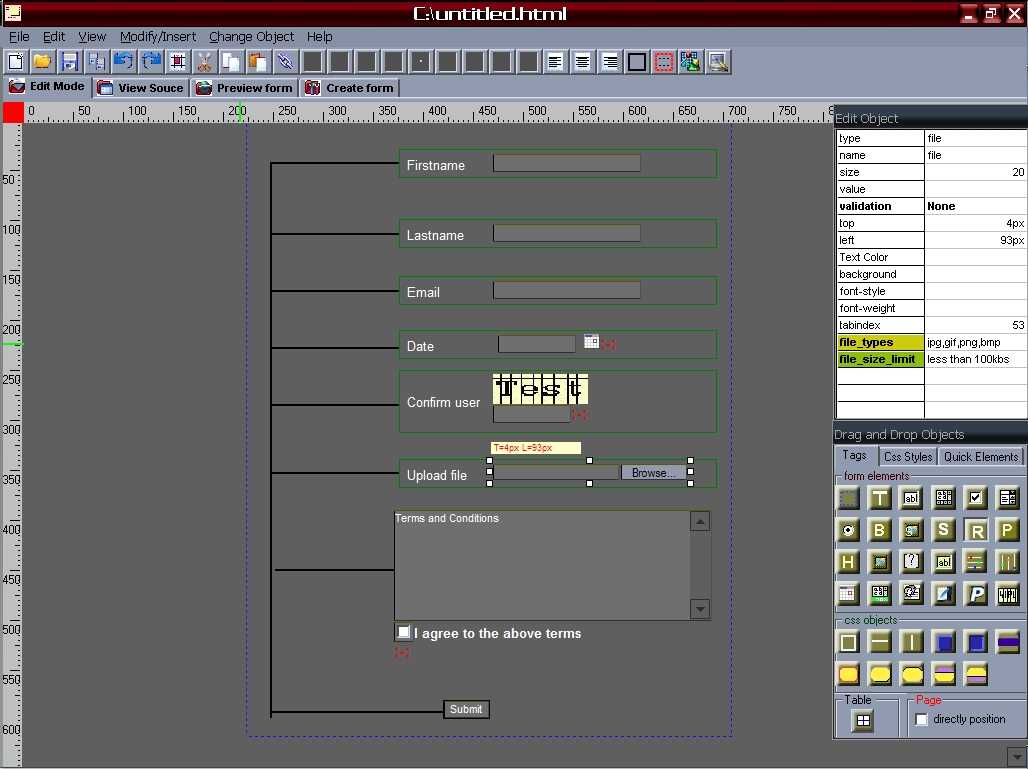 | Fast Forms is a visual tool utilizing drag and drop that creates and deploys HTML forms without you needing any knowledge of HTML or Internet coding. Fast Forms has been designed to take out all the coding involved in creating and capturing forms .. |
|
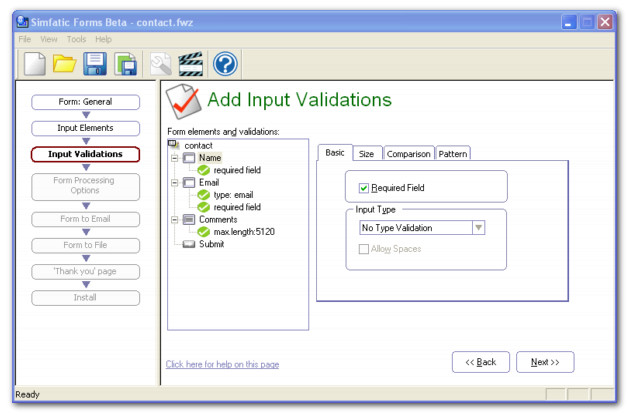 | Quickly create full featured forms complete with input validations using Simfatic forms. Receive the form submissions via email or saved to a file. You can install the form on your web server just by the press of a button. ..
|
|
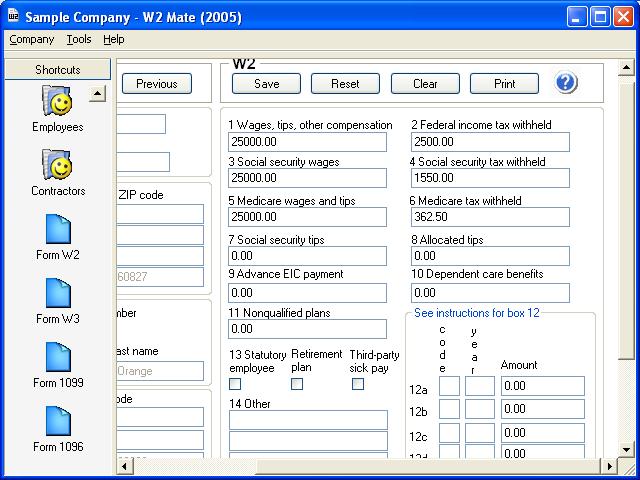 | W2 Mate is the easiest and fastest W2 and 1099 Forms printing software. W2 Mate prepares forms W2, 1099, W3 and 1096. Supports printing SSA-Approved laser substitutes for W2 Form Copy A and W3 on regular white paper, which eliminates the need for buying W2 and W3 forms. W2 Mate supports unlimited number of companies, forms, employees and recipients. The software prints on both white paper and on Red-Ink Laser forms, with the ability to adjust vertical and horizontal printing offset. .. |
|
 | This online divorce forms package is easy to download. The divorce online papers allow spouses to end their marriage at a low cost quickly. The divorce forms package includes marital settlement forms. .. |
|
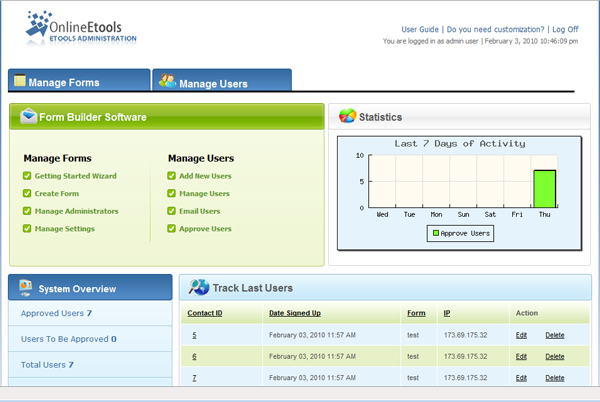 | The Omnistar Form Builder software is a dynamic web form builder for creating and managing forms on your site. The Omnistar Form Builder software allows you to create an email list campaign, customize html email templates, and manage mailing lists. .. |
|
 | Fill out PDF forms, save them and print them. You can add form fields to existing PDF files or fill out existing form fields. The program can also add comments to PDF files or highlight text in PDF files. Provide your customers with PDF forms they can fill out directly on the screen and print it out in Acrobat Reader! It is no longer necessary to print out the form in order to fill it out! The program adds form fields to pdf files. The form fields can filled out with the Acrobat Reader. It is easier for your customers to fill out the form and therefore even more customers will fill out your forms because they don't waste to much time. .. |
|
Results in Keywords For forms authentication timeout
 | This tool can adjust 3 'hidden' registry settings of Internet Explorer to control caching of DNS records, server connection timeout, and caching of server information.
It can be useful to change these settings to very low values, especially when testing web-servers with quickly changing DNS records / IP addresses. For example in DNS Round Robin or Simple Failover setups.
Internet Explorer does not honor and does not use the TTL (time to live) value provided in DNS records. Instead it caches all DNS records for a fixed period of time (as per this setting) - with one exception:
After Internet Explorer has fetched a web-page, it does not immediately close the TCP connection to the web-server. By keeping the connection open, following requests to the same web-server can be executed faster. This is known as 'keep alive'.
This setting affects both DNS caching and server connections ('keep alive') timeouts.
Internet Explorer does not refresh DNS records if another page is requested from the same server domain name within this time interval - even if the DNS Cache Timeout setting has a lower value.
In other words, DNS records timeout according to the higher value of this and the DNS Cache Timeout setting.
However, server connections appear to timeout according to the lower value of this and the Keep Alive Timeout setting.
So for the most predictable results, the value of this setting should be set lower than or equal to the DNS Cache Timeout setting, and higher than or equal to the Keep Alive Timeout setting... |
|
 | Basic Authentication is a little program that converts a user name (login) and optionally a password to/from their Base64 Basic Authentication counterpart...
|
|
 | The worlds first and only continuous real-time authentication system for the windows 2000 platform.Making use of NexRealm’s Behavior Recognition Technology, CLAM continuously monitors the system in real-time, making sure that the user accessing the system is indeed the genuine authorized user of the access account.Expensive biometric authentication hardware all have a fatal flaw, they use ‘once-off’ authentication. This means that once you have been authenticated the system is no longer protected.CLAM uses behavior patterns as the authentication ‘fingerprint’. The digital fingerprint profile enables CLAM to continuously protect the system in real-time. At anytime during the operation of the system, if an intruder tries to access the system, CLAM notices the difference of usage patterns and locks the .. |
|
 | A complete RADIUS authentication and accounting package based on Internet RFCs 2138 & 2139. It is designed to be easy to setup and use. TCCRadius provides for Authentication from ODBC, NT SAM, or Text. Fail-Safe Modes: rebuild your database automatically with Update Mode.Don.t ever have a sleepless night again because of authentication woes. If your database or RADIUS system fails, enable Accept Mode by changing one configuration option and TCCRadius will accept all ..
|
|
 | Pivo SSH was developed for commercial organization for securing remote shell access. The protocol supports compression and tunneling multiple TCP connections over one secured connection. Pivo SSH supports various authentication schemes such as password-based, public key or keyboard-interactive, allowing the client authorize itself using several schemes at the same time. Some SSH implementations also support PKI infrastructure for server and client authentication. PKI is a widely-used technology, so SSHBlackbox inlcudes PKIBlackbox for PKI support.
support for use of multiple authentication types at the same time flexible support for key validation.
Data transfer using events/callbacks, i.e. possibility to secure not only socket-based, but also other types of data exchange.
Asynchronous operation mode which lets you easily build synchronous and asynchronous applications... |
|
 | ACES Personalization Kit is a set of tools designed to enhance the Microsoft Internet Information Server or Microsoft Personal Web Server or any other server which supports ISAPI with additional authentication features.Includes ISAPI authentication filter configurable by Apache-like .htaccess files stored in site directories.Supports textual and OLEDB-accessible user databases, basic and cookie authentication, MD5 and DES password encryption, file masks and many other features.Also inludes COM components to access user data from ASP pages.This Kit make coding of your personalized and secure active server pages a ..
|
|
 | Cryptlib by Peter Gutmann is a security toolkit that allows even less experienced programmers to add strong encryption and authentication services to their programs, security features that are becoming more and more indispensable. The library attempts to hide the low-level details of encryption/decryption and authentication from programmers, allowing them to quickly make their projects more secure. Some of the symmetric encryption (private key) and authentication algorithms that cryptlib supports include the following:
.. |
|
 | The Maverick SSHD is an enterprise level multi-threaded Java SSH server. The product is compatible with Java 1.4 or later and uses the Java NIO framework for maximum server performance. SSH2 only is supported due to vulnerabilities in the earlier SSH1 protocol.
Features Include:
- Cross platform, 100% Java based component
- Supports JDK 1.4.2_05 and above
- SSH2 support only, for maximum security
- Supports SSH2 protocol only for maximum security
- SFTP & SCP file transfer protocols supported
- Scalable implementation based upon the Java NIO framework
- Reduce overheads by controlling your server's threading requirements
- Local and remote port forwarding fully supported
- Password authentication
- Public-key authentication
- Blowfish/3DES encryption ciphers
- Optional Twofish, AES & CAST ciphers (Requires additional configuration)
- SHA1/MD5 Message Authentication Codes (MACs)
- HTTP, SOCKS 4 and SOCKS 5 proxy support
- ZLIB Compression
- NativeAuthenticationProvider interface allows customization of the login process
- Abstract SessionChannel class allows customization of the shell and command execution
- NativeFileSystemProvider interface to customize file access
- Built in VirtualFileSystem provides platform independent NativeFileSystemProvider implementation
- VirtualFileSystem allows mounts to be defined by mapping virtual directories to physical folders.. |
|
 | Maverick.NET is a lightweight professional API for the Microsoft .NET framework. The product is written using 1000% managed C#, is compatible with all versions of the framework and supports SSH1, SSH2, SFTP and SCP. No external dependencies are required. Features included are: Product Information
* 100% fully managed component written in C# with no external dependencies
* Supports 1.0, 1.1 and 2.0 versions of the .NET Framework
* Full support for both SSH1 and SSH2 protocols
* Compatible with all SSH servers including SSH Communications Inc, OpenSSH, F-Secure and many others
* SFTP & SCP clients included
* Full MSDN-style API documentation
* Example code included in both VB.NET and C# languages
* Maximum 256-bit encryption using FIPS-197 AES cipher
* Password authentication
* Public key, keyboard-interactive authentication
* Port forwarding
* 3DES, Blowfish, AES, Serpent, Twofish and CAST ciphers
* diffie-hellman-group1-sha1 key exchange
* ssh-dss, ssh-rsa public keys
* SHA1, MD5 message authentication
* Interactive sessions
* Single threaded/threaded buffer modes
* State change events for client and channels
* Data listening events for asynchronous channel operation
* File transfer events for SFTP/SCP progress indicators
* Reading of PuTTY and SSH.com private keys
* X Forwarding.. |
|
 | SecureCRT is a Windows terminal emulator that supports Secure Shell (SSH), Telnet, rlogin, serial, and TAPI protocols. SSH provides encrypted login, terminal sessions, and data transfer. SecureCRT is highly customizable and easy to use.SecureCRT supports both SSH1 and SSH2 protocols. SSH2 support provides AES, 3DES, RC4, Blowfish, and Twofish ciphers, with password authentication, public-key authentication, and Kerberos v5 authentication via GSSAPI. Port forwarding allows redirecting TCP/IP applications over an encrypted channel. SecureCRT is ideal for connecting to remote systems running UNIX and VMS as well as the many BBSs and databases that are now available via the Internet. Remote sites can be easily accessed by just entering a hostname.Variable compression allows users with dialup connections to maximize performance. SSH2 server support includes the latest SSH2 servers from SSH Communications and OpenSSH. For easy multiple connections, SecureCRT can remember passphrases as long as the application is open. SecureCRT delivers quality emulations for VT100, VT102, VT220, ANSI, SCO ANSI, basic Wyse 50/60, Xterm and Linux console, with ANSI color support.Customization options include keymaps and login scripts, with many other choices including fonts, cursors, and color. Multi-byte character sets are supported for Japanese, Korean, and Chinese, as well as improved support for scalable line drawing fonts.Other features include the Activator utility for managing sessions from the system tray instead of the taskbar, session folders to manage hundreds of sessions, ActiveX scripting support for VBScript and other scripting languages, and secure file transfer using either the VCP command-line application or Zmodem. X11 forwarding enables encrypting X Windows sessions. SSH2 connections can be made from the command line using the included VSH program. Named sessions, auto logon, printing, emacs mode, and SOCKS firewall support are also popular features. .. |
|
Results in Description For forms authentication timeout
 | EZ-Forms-Contractor is the Filler, Printer, Viewer for Contractor and Construction Professional Related forms.
Forms were adapted for electronic fill-in/out, with print and save capability by EZ-Forms.
http://ez-forms.com/contractor.. |
|
 | Basic Authentication is a little program that converts a user name (login) and optionally a password to/from their Base64 Basic Authentication counterpart...
|
|
 | Texas Real Estate Forms, FormFiller, Printer, Viewer.
Forms were adapted for electronic fill-in/out, with print and save capability by EZ-Forms.
Sourced from TREC (Texas Real Estate Commission) Approved forms.
More@ http://ez-forms.com/txre.. |
|
 | Texas Real Estate Forms, FormFiller, Printer, Viewer. Forms were adapted for electronic fill-in/out, with print and save capability by EZ-Forms. Sourced from TREC (Texas Real Estate Commission) Approved forms. More@ http://ez-forms.com/txre..
|
|
 | Cryptlib by Peter Gutmann is a security toolkit that allows even less experienced programmers to add strong encryption and authentication services to their programs, security features that are becoming more and more indispensable. The library attempts to hide the low-level details of encryption/decryption and authentication from programmers, allowing them to quickly make their projects more secure. Some of the symmetric encryption (private key) and authentication algorithms that cryptlib supports include the following:
.. |
|
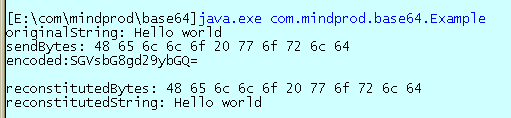 | Description - 32-bit application written in assembly that decodes clear text passwords used in Basic Authentication configurations. Basic Authentication is used by FTP and WEB servers..
|
|
 | A complete RADIUS authentication and accounting package based on Internet RFCs 2138 & 2139. It is designed to be easy to setup and use. TCCRadius provides for Authentication from ODBC, NT SAM, or Text. Fail-Safe Modes: rebuild your database automatically with Update Mode.Don.t ever have a sleepless night again because of authentication woes. If your database or RADIUS system fails, enable Accept Mode by changing one configuration option and TCCRadius will accept all .. |
|
 | EZ-Forms Express Filler for eforms (visual electronic forms) Fillout, Save, Modify, Print, Email, FAX(driver required), etc. eforms created with EZ-Forms ULTRA, EZ-Forms PRO, EZ-Forms Express Designers. Encryption enabled. Network/Internet compliant... |
|
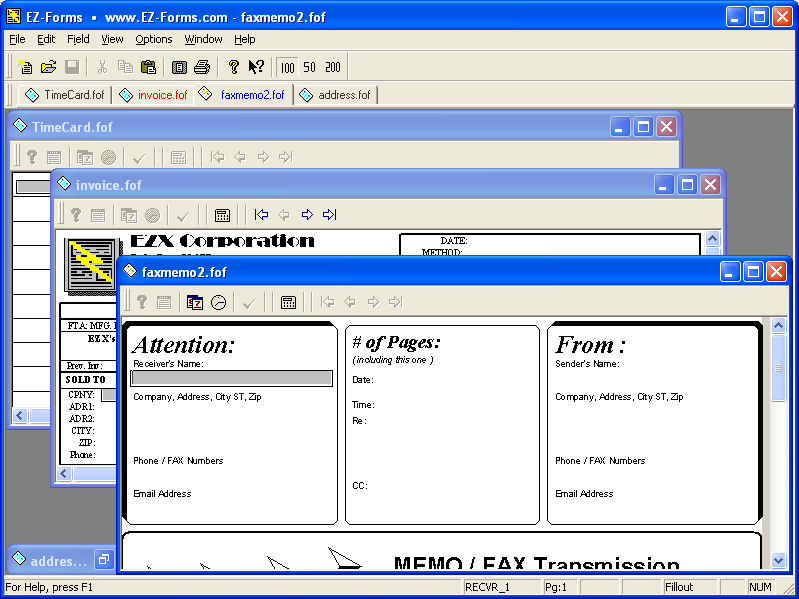 | EZ-Forms Express Filler for eforms (visual electronic forms) Fillout, Save, Modify, Print, Email, FAX(driver required), etc. eforms created with EZ-Forms ULTRA, EZ-Forms PRO, EZ-Forms Express Designers. Encryption enabled. Network/Internet compliant... |
|
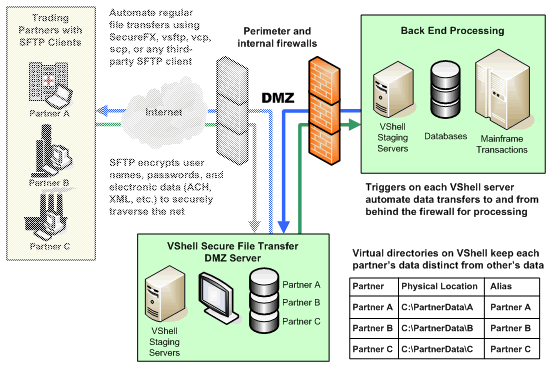 | VShell SSH2 server is a secure alternative to Telnet and FTP on Windows and UNIX providing strong encryption, robust authentication and data integrity. Fine-tune your environment with precision control and a selection of authentication methods... |
|
Results in Tags For forms authentication timeout
 | This tool can adjust 3 'hidden' registry settings of Internet Explorer to control caching of DNS records, server connection timeout, and caching of server information.
It can be useful to change these settings to very low values, especially when testing web-servers with quickly changing DNS records / IP addresses. For example in DNS Round Robin or Simple Failover setups.
Internet Explorer does not honor and does not use the TTL (time to live) value provided in DNS records. Instead it caches all DNS records for a fixed period of time (as per this setting) - with one exception:
After Internet Explorer has fetched a web-page, it does not immediately close the TCP connection to the web-server. By keeping the connection open, following requests to the same web-server can be executed faster. This is known as 'keep alive'.
This setting affects both DNS caching and server connections ('keep alive') timeouts.
Internet Explorer does not refresh DNS records if another page is requested from the same server domain name within this time interval - even if the DNS Cache Timeout setting has a lower value.
In other words, DNS records timeout according to the higher value of this and the DNS Cache Timeout setting.
However, server connections appear to timeout according to the lower value of this and the Keep Alive Timeout setting.
So for the most predictable results, the value of this setting should be set lower than or equal to the DNS Cache Timeout setting, and higher than or equal to the Keep Alive Timeout setting... |
|
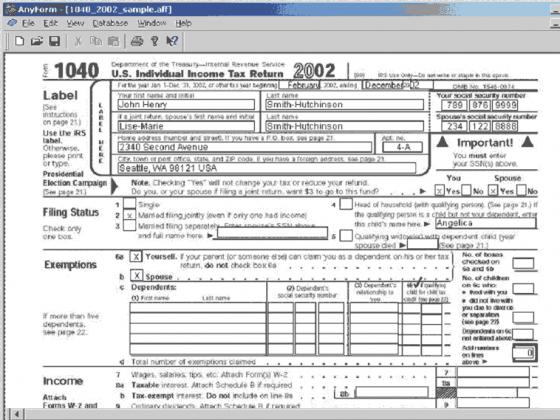 | Form software AnyForm..
|
|
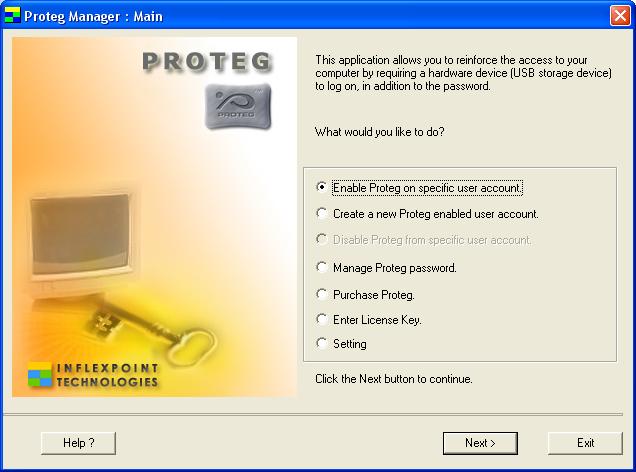 | Proteg is a security software that enables you to use your portable USB storage device (USB key, USB flash drive, thumbdrive) for secured Windows logon, authentication or access control - hence preventing unauthorized access... |
|
 | Stop memorising logins, passwords, Citrix servers and manually entering them; store all your Citrix connections on one USB flash drive, smart card, or token; enjoy automated access - simply insert the USB drive and pass convenient identification. Add the strength of multi-factor authentication for login to Citrix MetaFrame Presentation Server sessions, and eliminate the risks of passwords being lost, forgotten or stolen.
Users simply insert a smart card (or connect a USB flash to the computer) and, optionally, place a finger on a biometric scanner for gaining access to Citrix server. One hardware device, depending on its memory volume, can store many different connections using different user names and servers. User credentials can be securely stored not only on smart cards or USB tokens, but also on USB drives or other removable media (FDD, CD, CD/R, CD/RW, MO, MD, ZIP-disks, Pocket PCs, all types of flash memory cards) preserving the same functionality.
Features:
- No password problem: the need to remember connection details and passwords is eliminated.
- Simplified connection procedure: once configured to start specific connection on KSD insertion event, the connection becomes fully automatic and fast.
- Hardware variety: the ability to choose from a large list of supported devices, from different vendor' smart cards and tokens to ordinary USB flash drives, allows choosing the device which would best satisfy user's needs
- Mobility: The ability to store multiple connections on the same device allows users to enjoy even greater mobility already offered by Citrix.
- Secure Workstation: Dekart Logon for Citrix ICA Client can be configured to either lock the workstation (Disconnect) or to log off from Citrix server upon removal of the card, hardware token or USB drive;
- Multi-factor Authentication: users can be positively identified for access to Citrix-based resources via a wide range of digital identity credentials and biometric devices...
|
|
 | EZ-Forms Express Filler for eforms (visual electronic forms) Fillout, Save, Modify, Print, Email, FAX(driver required), etc. eforms created with EZ-Forms ULTRA, EZ-Forms PRO, EZ-Forms Express Designers. Encryption enabled. Network/Internet compliant... |
|
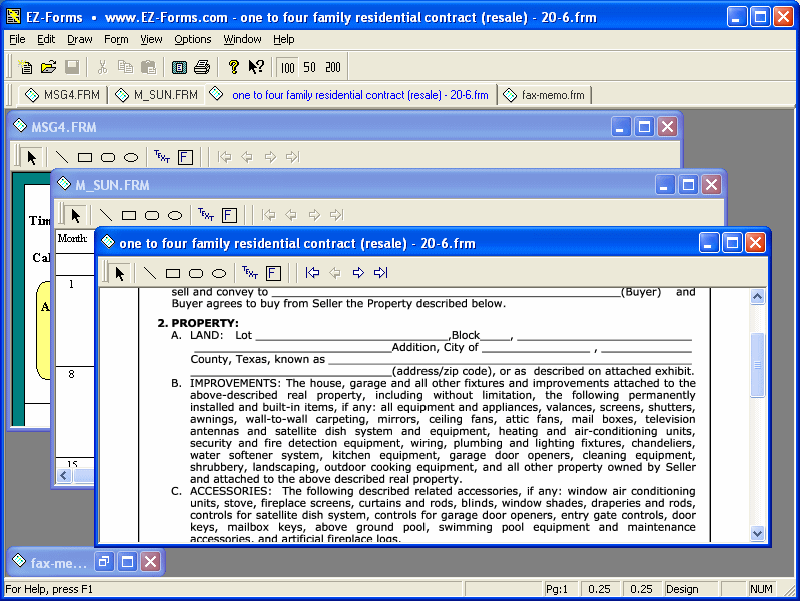 | As "EZ" as scan/import - point - click - insert/automate fields - go. Create Stand-alone electronic forms Pre-printed-form data-only overlay mode. Import PDFs (Acrobat), Bitmap Images Import/Export Data Encryption availabable Wizards make it EZ..
|
|
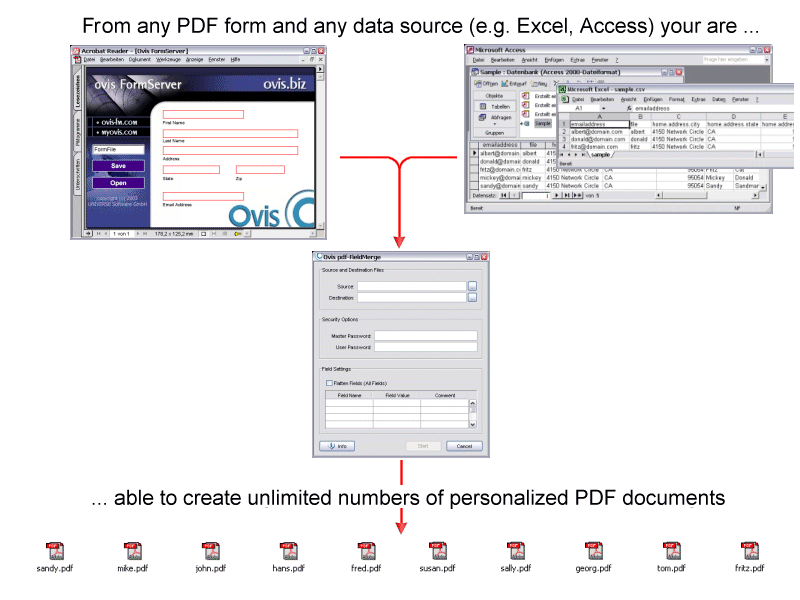 | With some few mouse clicks pdf-FieldMerge allows to fill in existing PDF form fields automatically. PDFs may be processed singularly or en masse - automatically or manually with pre-selected data - without detour of Acrobat Reader.. |
|
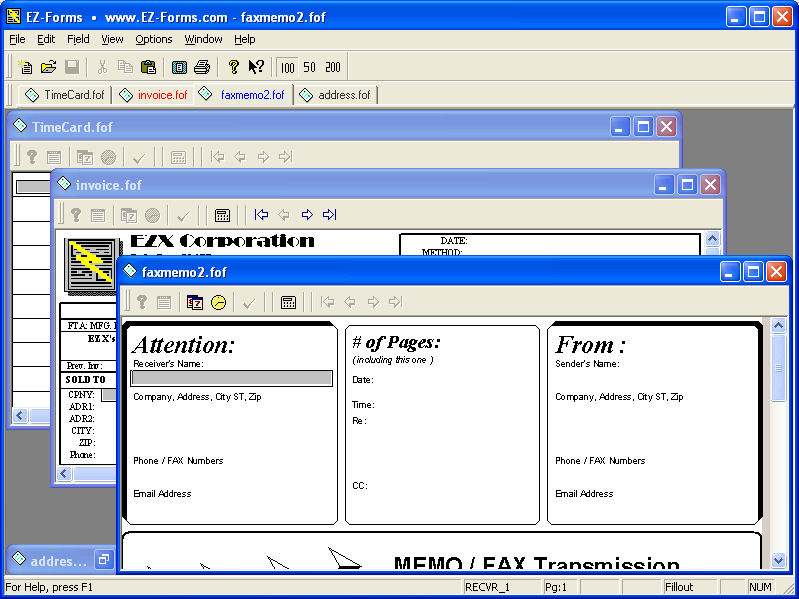 | EZ-Forms-Mortgage Forms, FormFiller, Printer, Viewer.
Forms were adapted by EZ-Forms.
More@ http://ez-forms.com/mortgage
The included Filler/Typer allows you to load up a form then fill it out by simply selecting the text tool, clicking to the location intended and typing.
. You will be able to modify text attributes like font, size and color with the selection (arrow) tool.
. You will even be able to add lines and boxes, if you wish.
. PDF compatible output available.
Visit: http://www.EZ-Forms.com/mortgage for more info... |
|
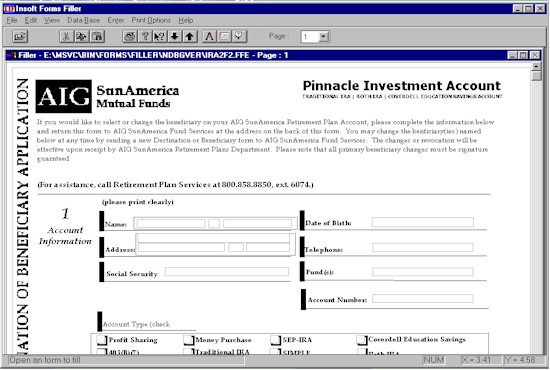 | Insoft Forms Filler software lets you replace existing or new paper forms with an unlimited supply ofmulti-page WYSIWYG electronic forms, with data validation, computation etc., making it easier to fill and print forms quickly... |
|
 | Unplugged is a very simple tool for letting you know when your internet connection has suddenly become unavailable. Gives you visual and verbal warnings if you become disconnected. Free with sign up for web services. See buy now page for details... |
|
Related search : original paper formodbc supported databaseimporting data fromfactor authenticationunauthorized access,factor authentication systemusb flashica clientcitrix icalogon fordekart logon,multi factor authenticationforms ultraforms express,forms express desOrder by Related
- New Release
- Rate
request timeout -
iis timeout -
timeout period -
idle timeout -
session timeout -
|
|





























